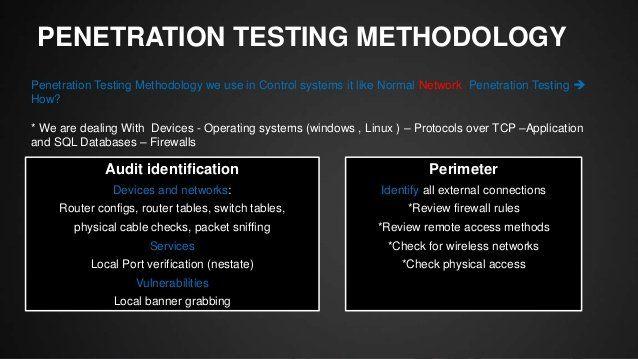
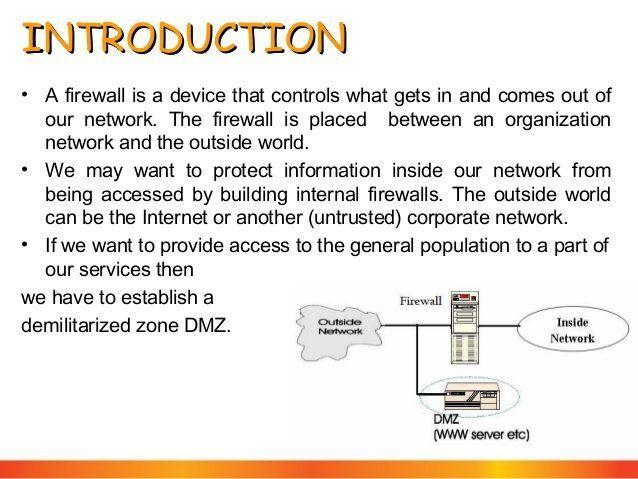
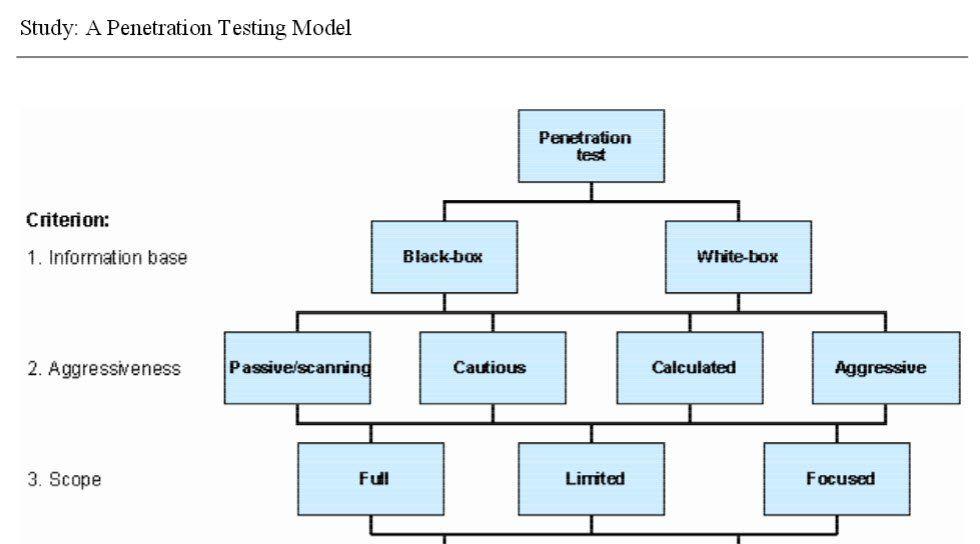
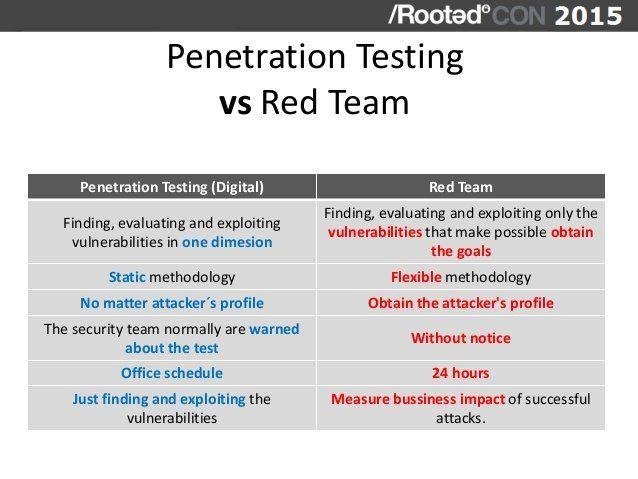
Firewall penetration testing methodology



I Rhoda Age: 22. Hi I'm Sara if you looking for a sexy and hot girl then you are in the perfect placeHi I'm Sharon, a TS escort based in San Francisco



Ask Yourself


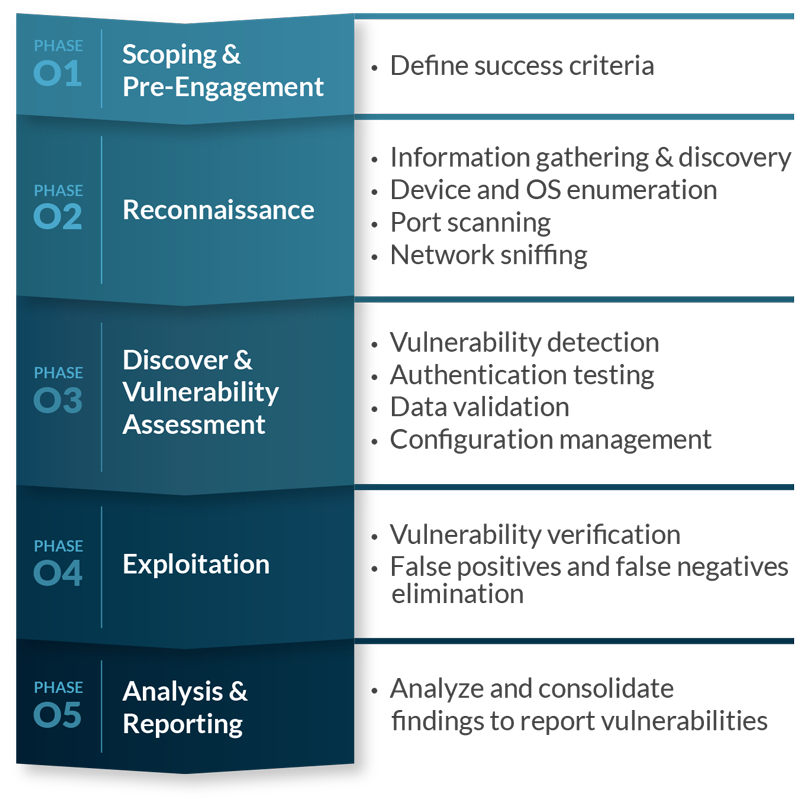
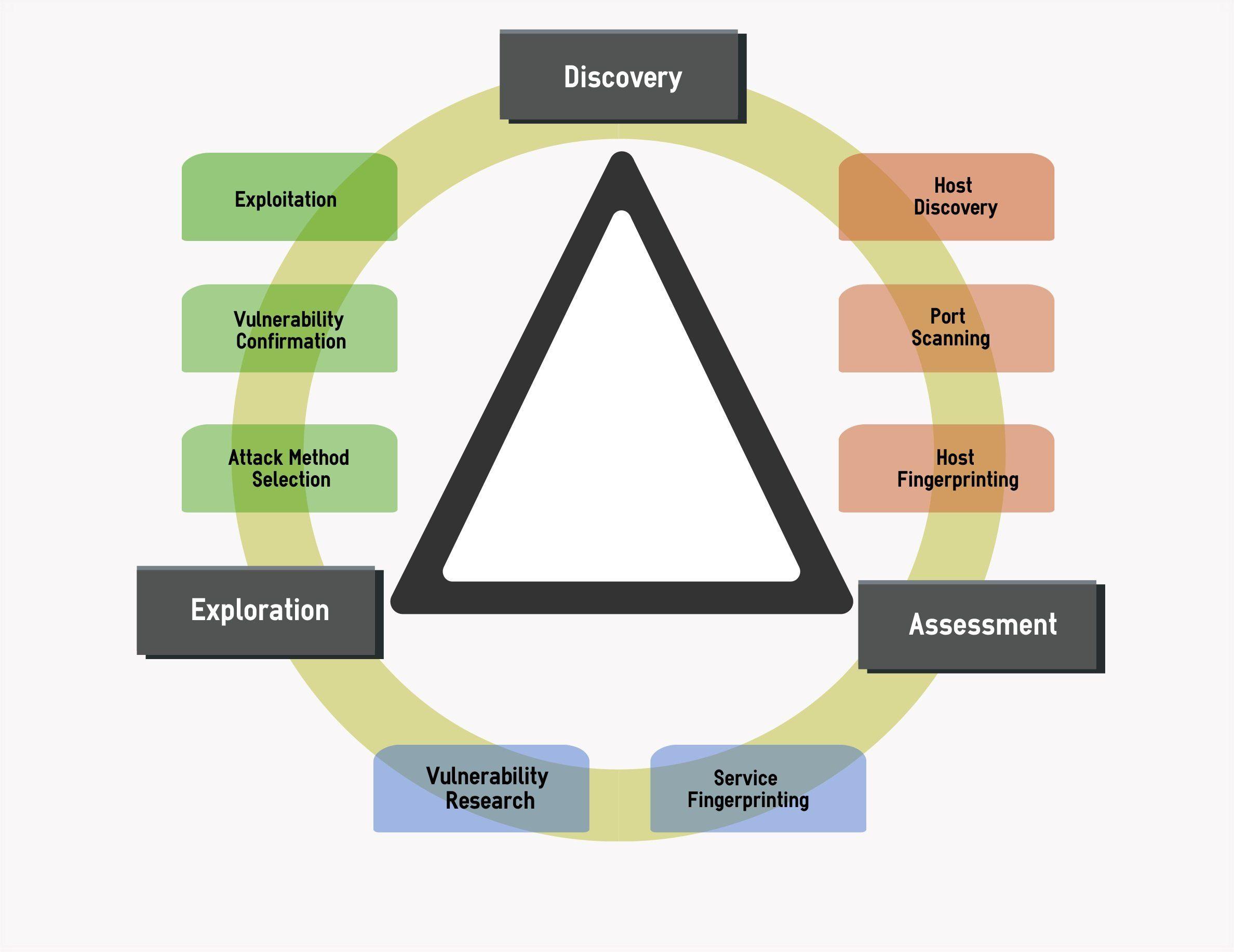
In this paper, I describe a methodology to perform firewall penetration testing. Before we perform the actual testing, I also discuss hot to decide who will perform it.



Firewall Security Testing

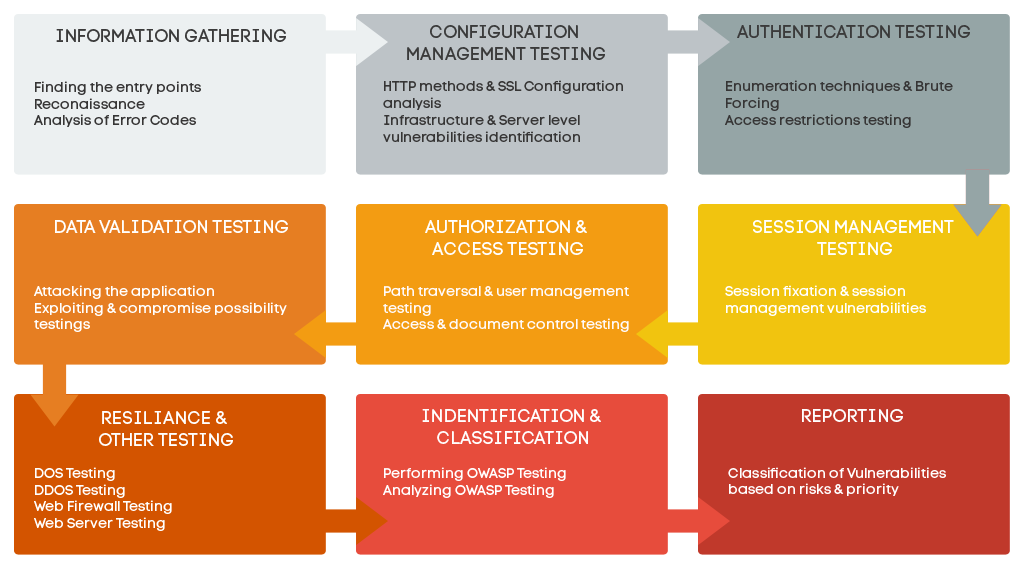
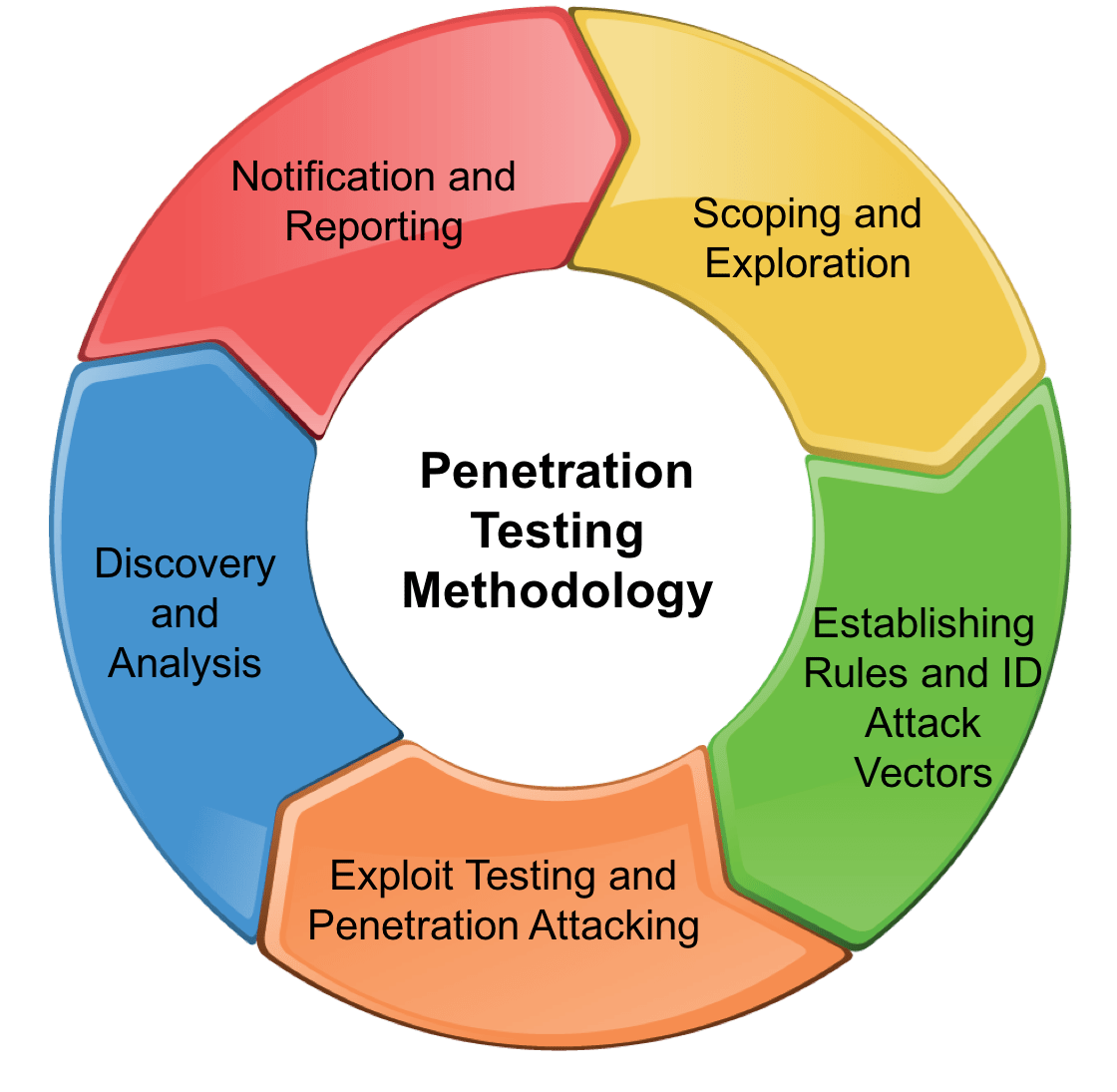

Description:Generally, most modern firewalls filter such ACK requests. An example command with hping is: Port 53 or 20 are often used as a testing source port. Vendors are much more security aware than in previous years and products now thankfully reflect a more security conscious environment and internet. Tomahawk is useful to test the network throughput of network hardware: Once any threats highlighted in the report have been remediated, you can schedule a re-test of those elements. If allowed at the firewall, an ACK scan can report back if a port is being filtered or unfiltered.
































User Comments 1
Post a comment
Comment: