Penetration testing tool


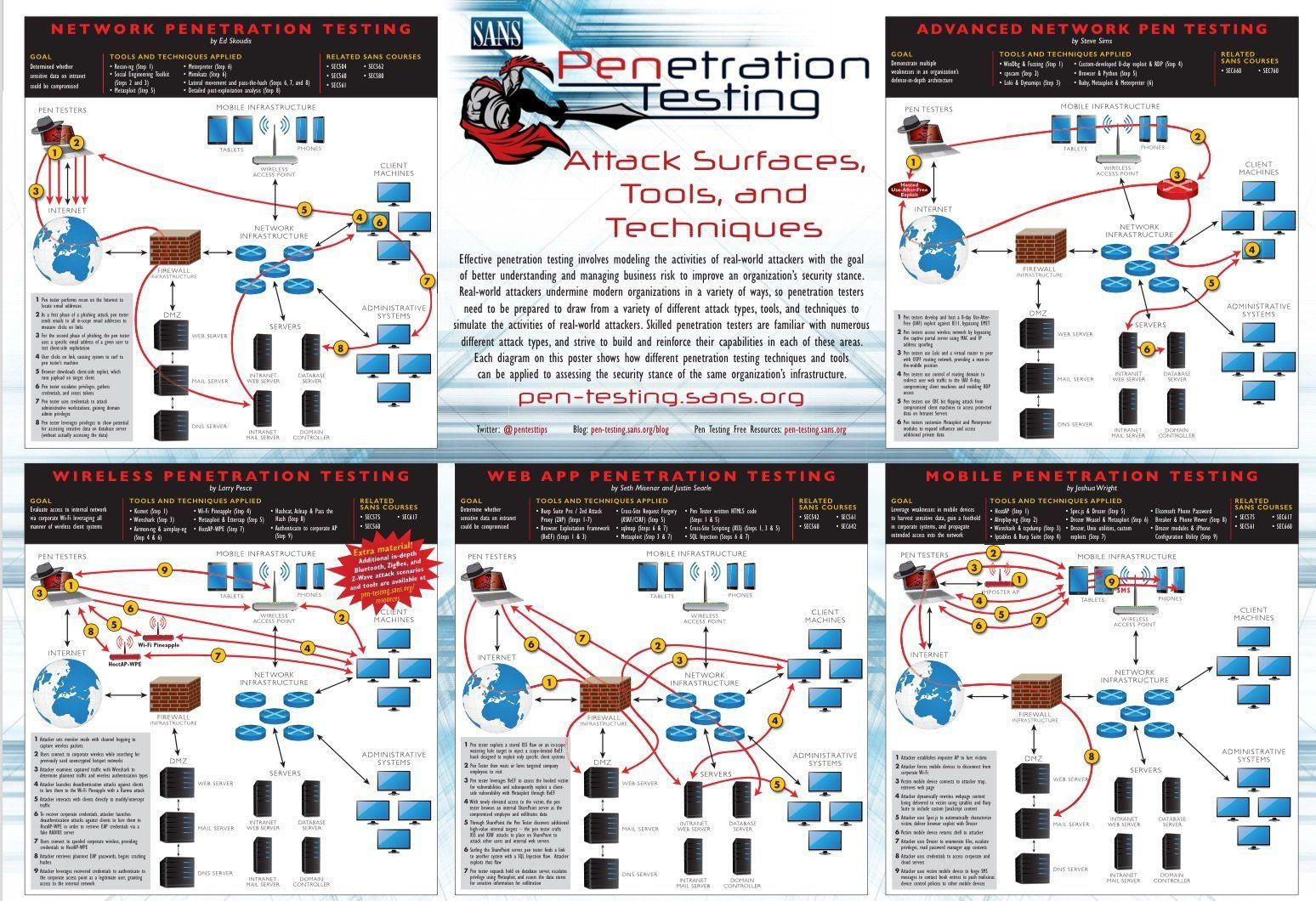
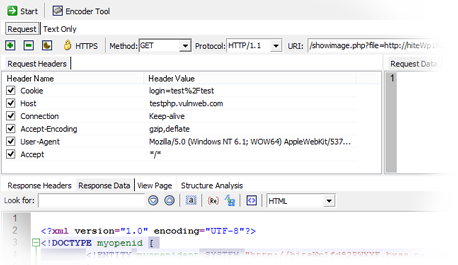
What is Penetration Testing? Tools and Techniques | Rapid7

Hi guys Reanna Age: 20. I am romantic, and i prefer places with a sophisticated atmosphere and love pleasant conversations with interesting and well educated people.


How this service works





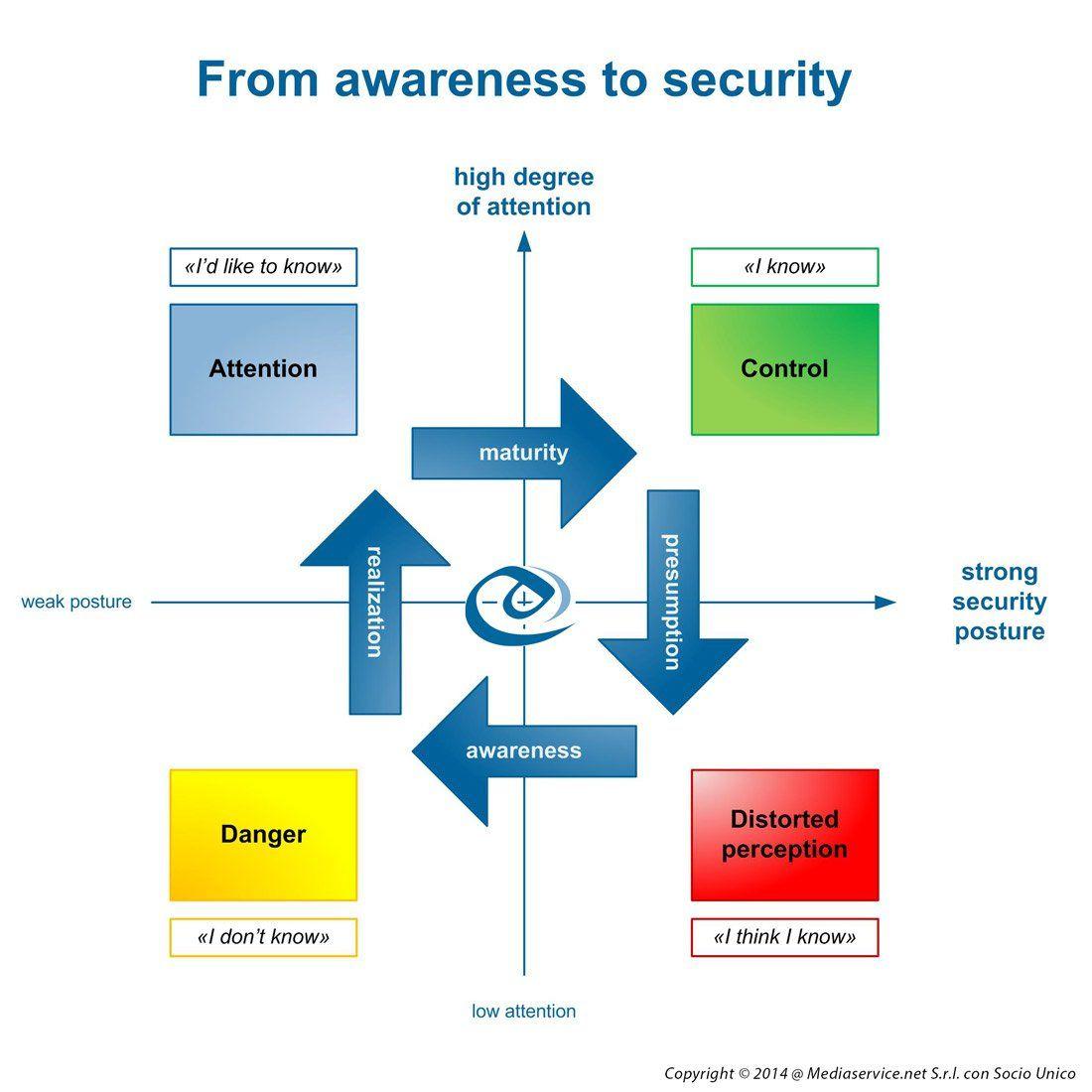
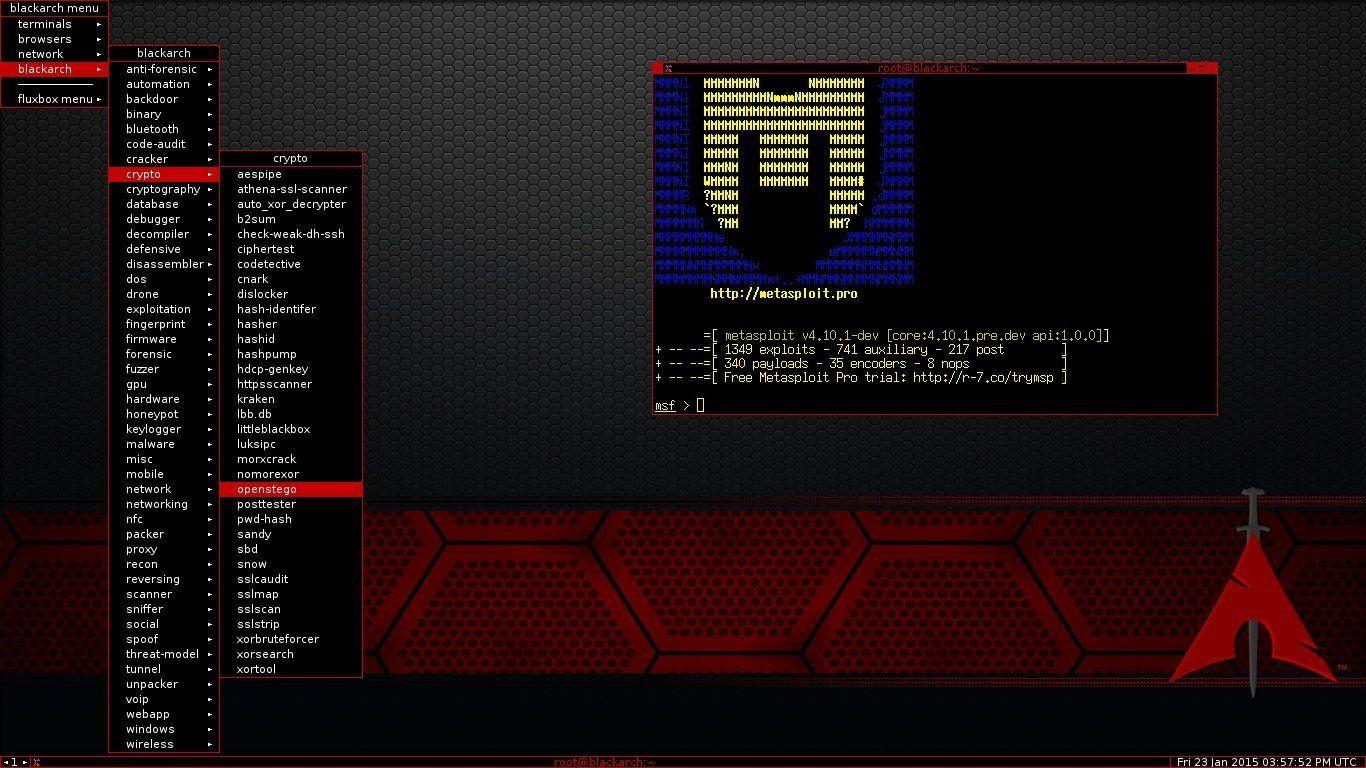
Penetration Testing Tools present in Kali Linux
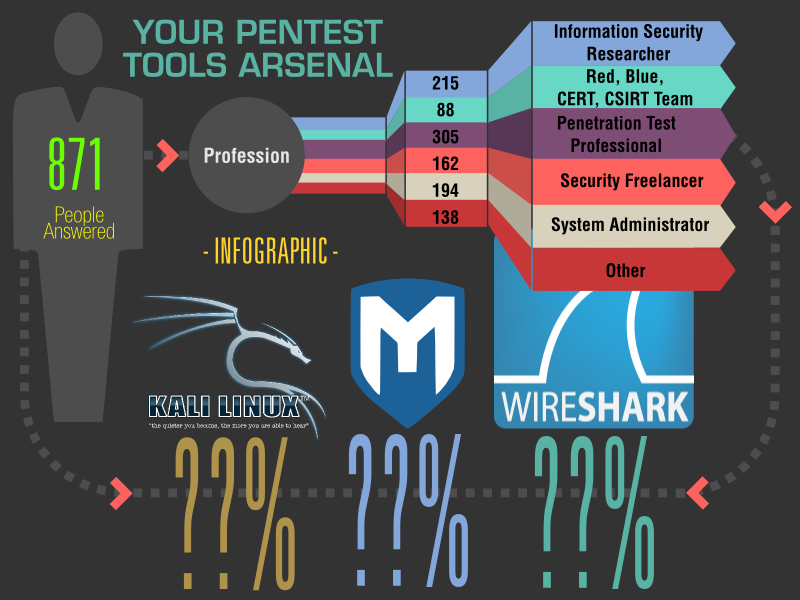
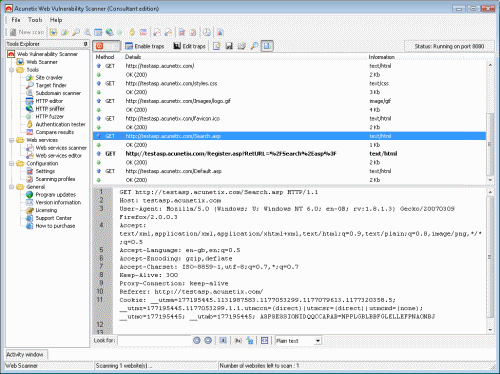
16 Apr A list of all the best and most popular Pen Testing/Security Testing tools required for every penetration tester is addressed in this article. Wouldn't it be fun if a company hired you to hack its website/ network/ Server? Well, Yeah! Penetration testing, commonly known as pen-testing is on a roll in the testing.
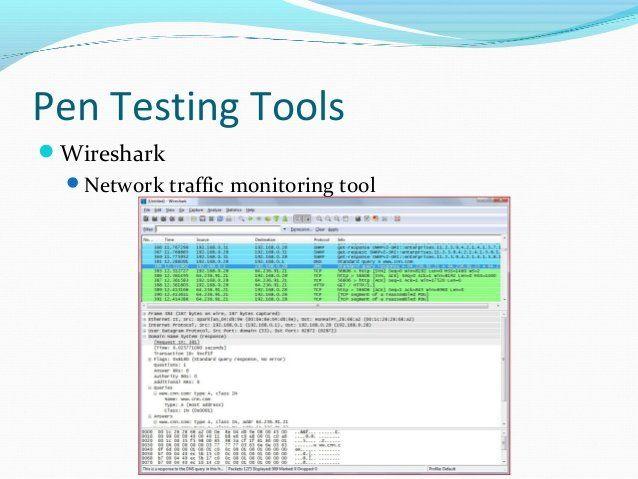

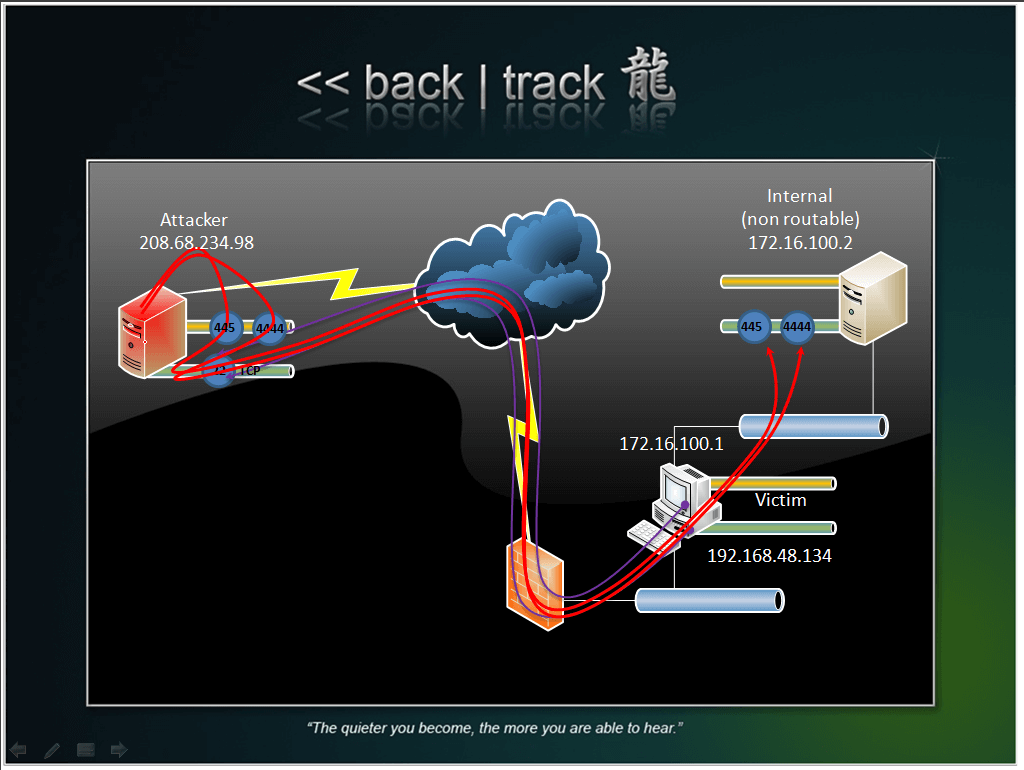
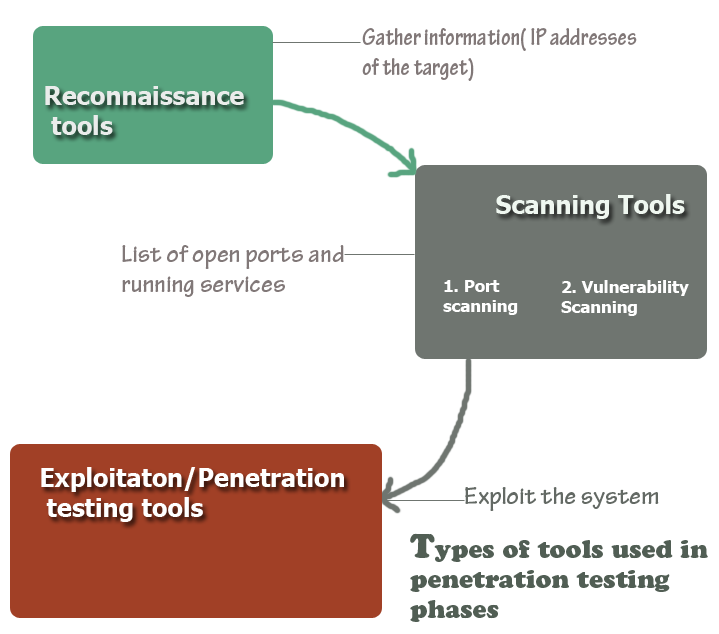


Jess Age: 23. With possibility of sessions bdsm in equipped study all europe .direct to hotel roomIf you are seeking for a dominant woman who can play with your mind and body, if you want to become her sex toy, her pet, her slave, if you need to be disciplined or crave worshiping a beautiful goddess, then look no further! You need me and i want to own you.
Description:What Is Penetration Testing? Penetration Testing Defined There is a considerable amount of confusion in the industry regarding the differences between vulnerability scanning and penetration testing, as the two phrases are commonly interchanged. However, their meaning and implications are very different. A vulnerability assessment simply identifies and reports noted vulnerabilities, whereas a penetration test Pen Test attempts to exploit the vulnerabilities to determine whether unauthorized access or other malicious activity is possible. Penetration testing typically includes network penetration testing and application security testing as well as controls and processes around the networks and applications, and should occur from both outside the network trying to come in external testing and from inside the network.
































User Comments 1
Post a comment
Comment: